Network Design, Ports, and Flows
Redpanda Cloud deploys two different types of networks: one for private Redpanda clusters and another for public Redpanda clusters. By default, networks are always laid out across multiple availability zones (AZs) to enable the creation of one or many single and multi-AZ Redpanda clusters within them.
Public Redpanda clusters
With public Redpanda clusters, TCP listeners are protected by SASL/SCRAM (SCRAM-SHA-256, SCRAM-SHA-512) authentication and encrypted in transit using TLS 1.2.
The following diagram shows the public subnet used by public Redpanda clusters.
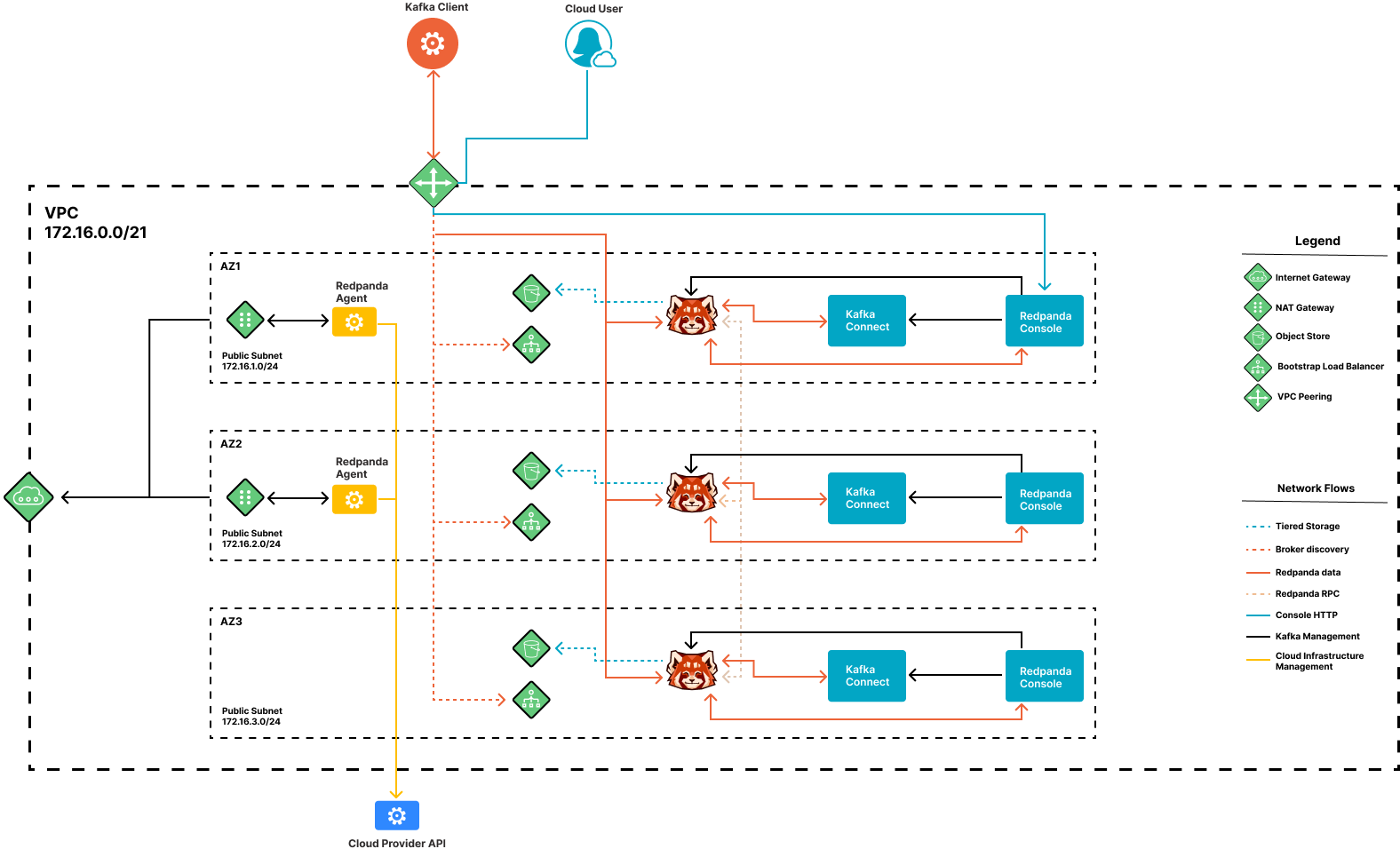
Private Redpanda clusters
Private Redpanda clusters are designed based on the following behaviors:
-
There is proper network segmentation.
-
All Redpanda services are only accessible from within the same VPC or through VPC peering.
-
The data plane agent is placed in public subnets and segmented away by firewall rules from Redpanda services.
The following diagram shows the private subnet used by private Redpanda clusters.
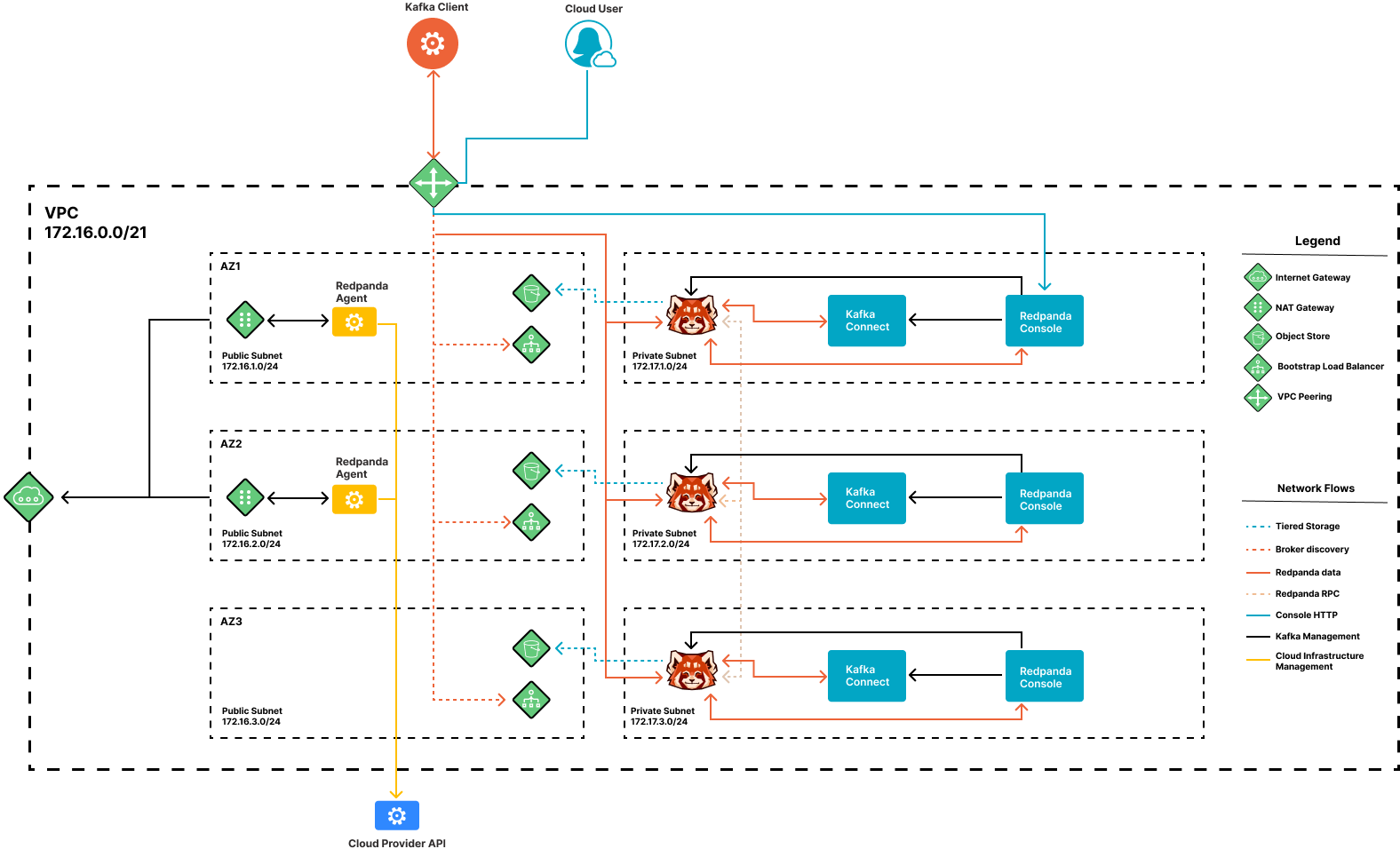
Network ports
Network ports are available for North-South, East-West, and South-North as follows.
North-South
The following table lists the network ports available to external clients within each data plane. For private-only Redpanda clusters, access to these ports is only possible through Redpanda Cloud network connections such as VPC Peering, transit gateway attachments, or private links.
| Service | Port |
|---|---|
Kafka API |
30092/tcp |
Kafka bootstrap |
9092/tcp |
Schema Registry |
30081/tcp |
HTTP Proxy |
30082/tcp |
Redpanda Console, Prometheus metrics |
443/tcp |
East-West
The following table lists the network ports available within each data plane for internal communication only.
| Service | Port |
|---|---|
Kafka API |
30092/tcp |
Kafka bootstrap |
9092/tcp |
Schema Registry |
30081/tcp |
HTTP Proxy |
30082/tcp |
Redpanda Console |
33145/tcp |
Redpanda Admin API |
30644/tcp |
Kafka Connect API |
8083/tcp |
AWS network services
Redpanda Cloud supports the following Amazon Web Services (AWS) network services.
-
Time synchronization
To ensure time synchronization, Redpanda Cloud in AWS uses the Amazon Time Sync Service, a fleet of redundant satellite-connected and atomic reference clocks in AWS regions.
-
Domain Name System (DNS)
Redpanda Cloud creates a new DNS zone for each cluster in the control plane and delegates its management exclusively to each cluster’s data plane. In turn, the data plane creates a hosted zone in Route 53, managing DNS records for Redpanda services as needed. All interactions with Route 53 are controlled by IAM policies targeted to the specific Route 53 resources managed by each data plane, following the least privilege principle.
-
Distributed denial of service (DDoS) protection
All Redpanda Cloud services publicly exposed in the control plane and data plane are protected against the most common layer 3 and 4 DDoS attacks by AWS Shield Standard, with no latency impact.
-
VPC peering
Redpanda Cloud supports configuring VPC peering against Redpanda Cloud networks, making them available to one or many private clusters and allowing users to connect to those clusters without traversing the public internet.
You can establish VPC peering connections between two VPCs with non-overlapping network addresses. When creating a network intended for peering, ensure that the specified network address range does not overlap with the network address range of the destination VPC.
It is strongly recommended to reject all network traffic initiated from a Redpanda Cloud network and only accept traffic from Kafka connectors that connect to your internal data stores to retrieve or push data.
GCP network services
Redpanda Cloud supports the following Google Cloud Platform (GCP) network services.
-
Time synchronization
To ensure time synchronization, Redpanda Cloud in GCP uses Google NTP Servers, a fleet of satellite-connected and atomic reference clocks.
-
Domain Name System (DNS)
Redpanda Cloud creates a new DNS zone for each cluster in the control plane and delegates its management exclusively to each cluster’s data plane. In turn, the data plane creates a managed zone in Cloud DNS, managing DNS records for Redpanda services, as needed. All the interactions with Cloud DNS are controlled by IAM policies targeted to the specific Cloud DNS resources managed by each data plane, following the least privilege principle.
-
VPC peering
Redpanda Cloud supports configuring VPC peering against Redpanda Cloud networks, making them available to one or many private Redpanda clusters and allowing users to connect to those clusters without traversing the public internet.
You can establish VPC peering connections between two VPCs with non-overlapping network addresses. When creating a network intended for peering, ensure that the specified network address range does not overlap with the network address range of the destination VPC.
It is strongly recommended to reject all network traffic initiated from a Redpanda Cloud network and only accept traffic from Kafka connectors that connect to your internal data stores to retrieve or push data.